Is Your Business a Cyber Attack Waiting to Happen?
Find Out with Our FREE CyberFit™ Health Check
HOW WE HELP
AiPenTest
Network Penetration Testing

Network Penetration Testing with AiPenTest: Affordable, Accurate, and Super Quick.
Unlock swift and precise Network Penetration Testing with AiPenTest, where affordability meets cutting-edge technology. Benefit from cost-effective security assessments, meticulously accurate, delivered to your inbox within 48 hours post-assessment. Our AI-driven service ensures rapid turnaround without sacrificing precision, giving you the critical insights needed to fortify your network efficiently and economically.
AiPenTest Solves Today's
CHALLENGES
AiPenTest streamlines cybersecurity efforts, saving on the substantial costs typically associated with traditional penetration testing.
By delivering comprehensive reports within 48 hours, AiPenTest addresses the need for swift security assessments, enabling prompt response to vulnerabilities.
AiPenTest serves as an expert in your corner, providing top-tier security analysis without the need for in-house technical know-how.
AiPenTest keeps pace with the latest cyber threats, offering peace of mind that your defences are up-to-date and effective.
AiPenTest helps maintain regulatory compliance, reducing the risk of costly legal and financial repercussions from data breaches.
PRE AND POST BREACH SIMULATION
AiPenTest can perform pre and post breach simulations at any time within both the internal and external network environments.
Open Source Intelligence Gathering - Leveraging publicly available information from the internet, such as employee names and email addresses, to mount successful attacks against the organisation's environment.
Host Discovery - Scanning the target environment to find active systems and check open ports, which identifies what services are running.
Enumeration - Checking systems and services to find useful details, like weak spots that could be targets for attacks.
Exploitation - Combining details from online research, system scanning, and services checks, AiPenTest actively launches attacks against the vulnerable services by trying
password-based attacks, man-in-the-middle (MitM) attacks, relay attacks, and other advanced tactics.
Post-Exploitation - After successfully gaining initial access to a system, AiPenTest moves to automatically execute privilege escalation attacks. Simultaneously, it explores additional pathways, scrutinising the environment for opportunities to further penetrate the network or access confidential data. This strategic approach ensures a thorough assessment of potential vulnerabilities and the extent to which an attacker could exploit the system.
Backed by Experience
Access expert penetration testing skills on-demand. Outsmart cyber threats before they strike.
Unleash expert-level cybersecurity with our certified team (eCPPT, OSCP, OSCE, CREST). Decades of experience and 13+ industry certifications power our streamlined network penetration tests. Outsmart threats with our efficient, actionable approach. Be Secure. Be Fast. Be the Hacker.




Your Cyber Security Action Plan: Delivered Within 48 Hours
Receive a comprehensive report with tailored recommendations.
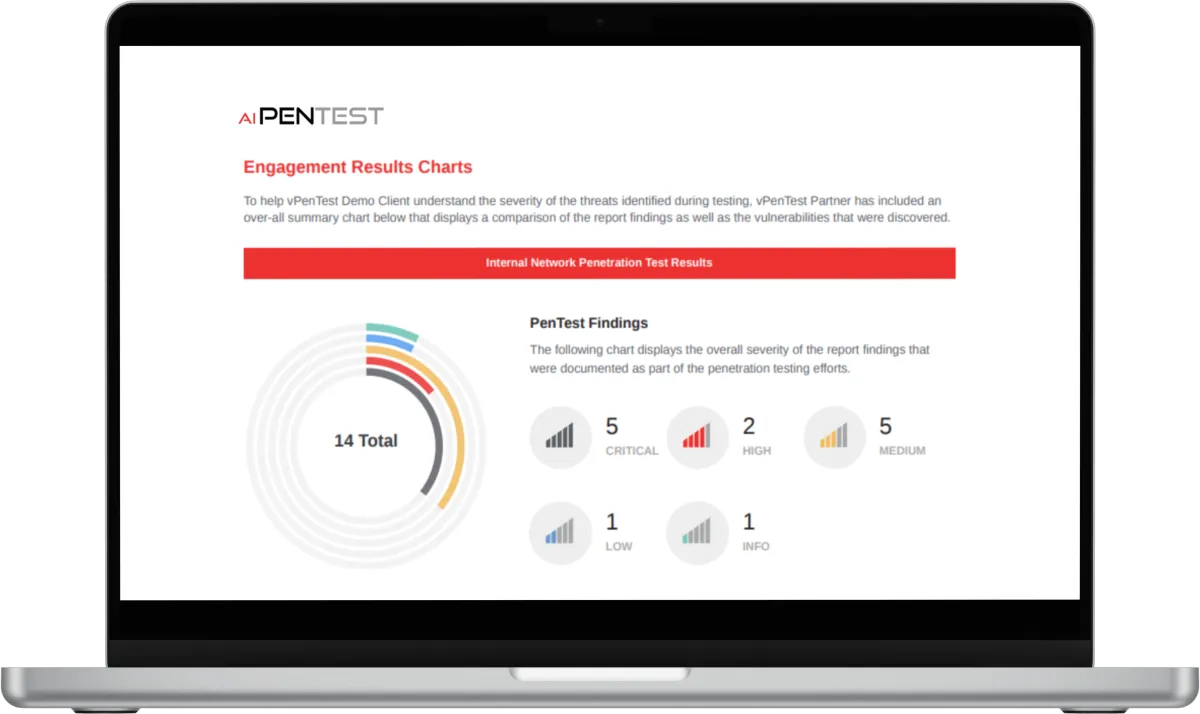
Following your penetration test, you'll receive a comprehensive report within 48 hours, detailing our findings, including:
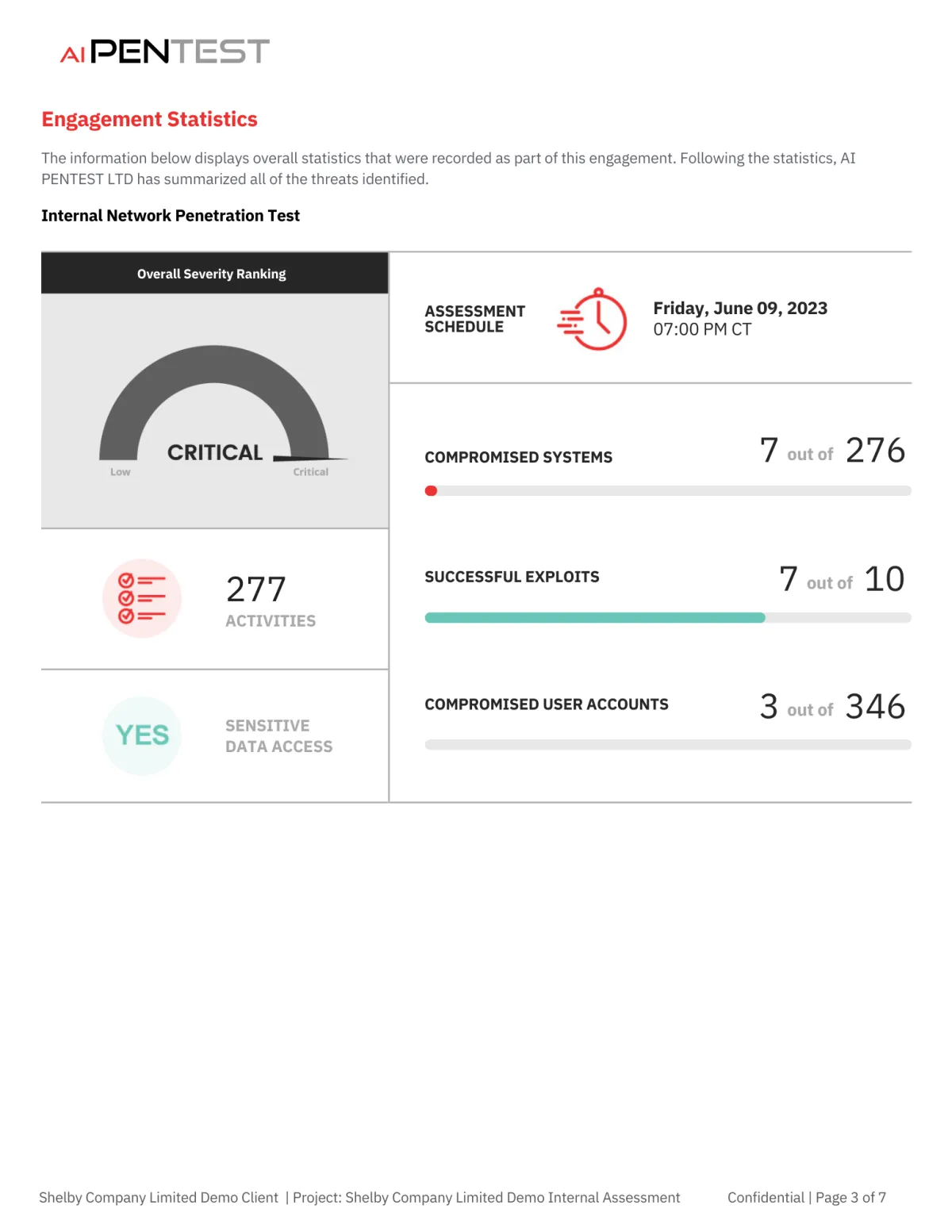
Identified vulnerabilities: Clearly explained weaknesses in your network security.
Prioritised recommendations: A clear road-map for mitigating each risk, tailored to your specific business needs.
Security impact assessment: The real-world consequences of each vulnerability, highlighting potential risks to your business.
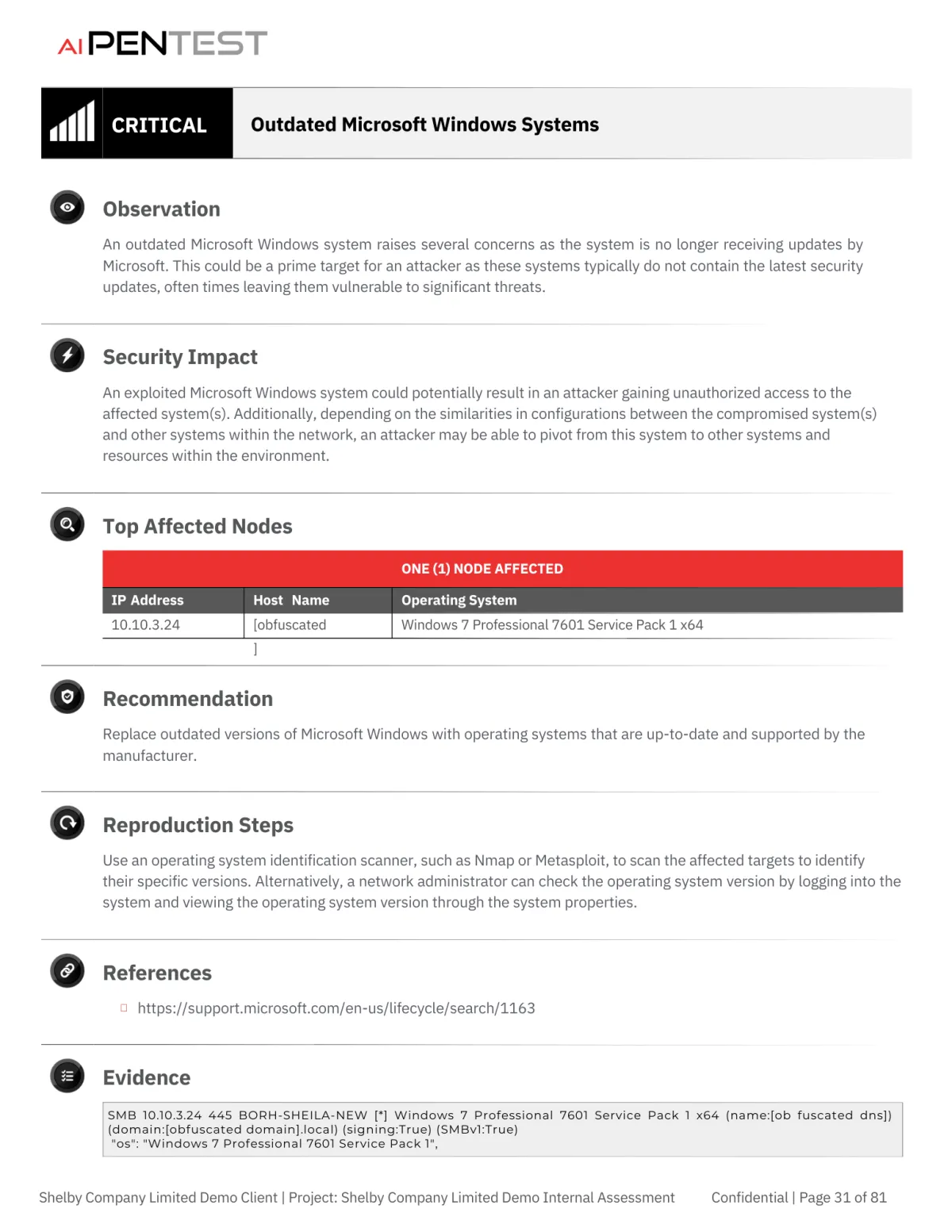
Step-by-step reproduction: Detailed instructions and screenshots demonstrating how vulnerabilities were discovered, providing concrete evidence for further investigation.
Additional resources: Links to relevant articles, guides, and tools to help you further understand and address each vulnerability.
DOES IT REALLY WORK?
AiPenTest penetration testing service distinguishes itself by its exhaustive approach, frequently uncovering numerous vulnerabilities and credential-related issues.
Unlike traditional manual network penetration tests, which may stop upon discovering a singular issue in a given device or service, our method continues to find and exploit vulnerabilities ensuring a comprehensive evaluation.
Within 48 hours, you'll receive a detailed PDF report featuring an executive summary and actionable recommendations to address and rectify the identified vulnerabilities.
In addition to the report, we provide a complimentary retest, which can be scheduled at your convenience. This retest is designed to verify that the issues have been resolved, giving you confidence in your security measures. Furthermore, we offer optional professional services to remediate these vulnerabilities, ensuring your utmost security and peace of mind.

Want to Know More About Network Pen Testing?
At last, a cost-effective answer to the complex search for quality network penetration testing. Explore how AiPenTest outperforms traditional penetration test services, offering superior value and easing the burden for businesses.

What is network penetration testing?
Network penetration testing simulates a cyberattack on an organisation's network to uncover and address security gaps. Think of it as a controlled hacking exercise aimed at discovering how a real attacker could breach the system and cause harm. The objective is to spot and rectify these vulnerabilities before an actual malicious hacker can exploit them, serving as a proactive measure to ensure the network's security integrity.
What is involved in a pen test?
During network penetration testing, several attempts are made to exploit security vulnerabilities with the ultimate goal of gaining access to data and systems. This involves exploiting issues like outdated patches, authentication flaws, incorrect settings, and targeting users via man-in-the-middle attacks. Following a successful breach, post-exploitation activities occur, which typically include privilege escalation, lateral movement, and enumeration of accessible resources to find sensitive data.
How often should an organisation conduct a penetration test?
How often to run penetration tests should be based on the organisation's risk profile, how sensitive its data is, and how it operates. Ideally, organisations should perform penetration tests at least once a year, but doing it twice a year is recommended. Additionally, tests should be conducted after any significant changes to their systems or networks.
What are some common challenges with pen testing?
Penetration testing often faces challenges such as incorrect threat alerts (false positives), a shortage of skills or resources, and pushback from stakeholders who see the tests as interruptions to their work.
With CloudLinxed's AiPenTest service, all of these issues are eliminated.
What is the difference between a penetration test and a vulnerability scan?
Vulnerability scanning is an automated process that identifies known vulnerabilities in systems and networks but does not test the effectiveness of security controls. Unlike basic vulnerability scans, our AiPenTest service actively exploits identified vulnerabilities in a controlled manner to replicate real-world attack scenarios. This approach not only identifies weaknesses but also tests the resilience of the systems against actual hacking attempts, offering a more realistic assessment of security vulnerabilities.
What is the difference between AiPenTest compared to a traditional network penetration test?
Traditional manual penetration testing processes are notably labor-intensive and slow. In contrast, AiPenTest operates multiple tools at once, automatically processes the outcomes, and strategically plans its next steps, significantly reducing the time usually spent on sequential commands. Additionally, AiPenTest slashes the reporting time, which typically encompasses reporting, quality assurance, and more, from an average of 6 hours to under a minute. This efficiency translates to an astonishing 29,900% increase in speed per assessment, streamlining the entire process.
What should you do after a pen test?
Following a penetration test, the specialists at AiPenTest will deliver a comprehensive report, complete with detailed recommendations and the professional services required for remediation. We prioritise the identified vulnerabilities, create a plan for their resolution, and perform ongoing re-testing to confirm that these issues have been effectively resolved.
Does AiPenTest cover MITRE ATT&CK types?
Indeed, the AiPenTest service effectively simulates several attack techniques outlined in the MITRE ATT&CK framework.
IS YOUR BUSINESS CYBER-FIT? FIND OUT NOW!
If your organisation takes cyber security seriously, schedule your FREE CyberFit™ Assessment with us today.

Boost your business with AiPenTest: The leading provider of next-generation penetration testing services. Experience cutting-edge cybersecurity support that sets you apart. Together, let's secure and advance your digital future and say goodbye to manual network pen testing – the future is automated!
Company Registered in England and Wales 15056389
CONNECT WITH US
Follow us on social media for the latest AiPenTest updates, announcements, and cybersecurity best practices from our security experts.